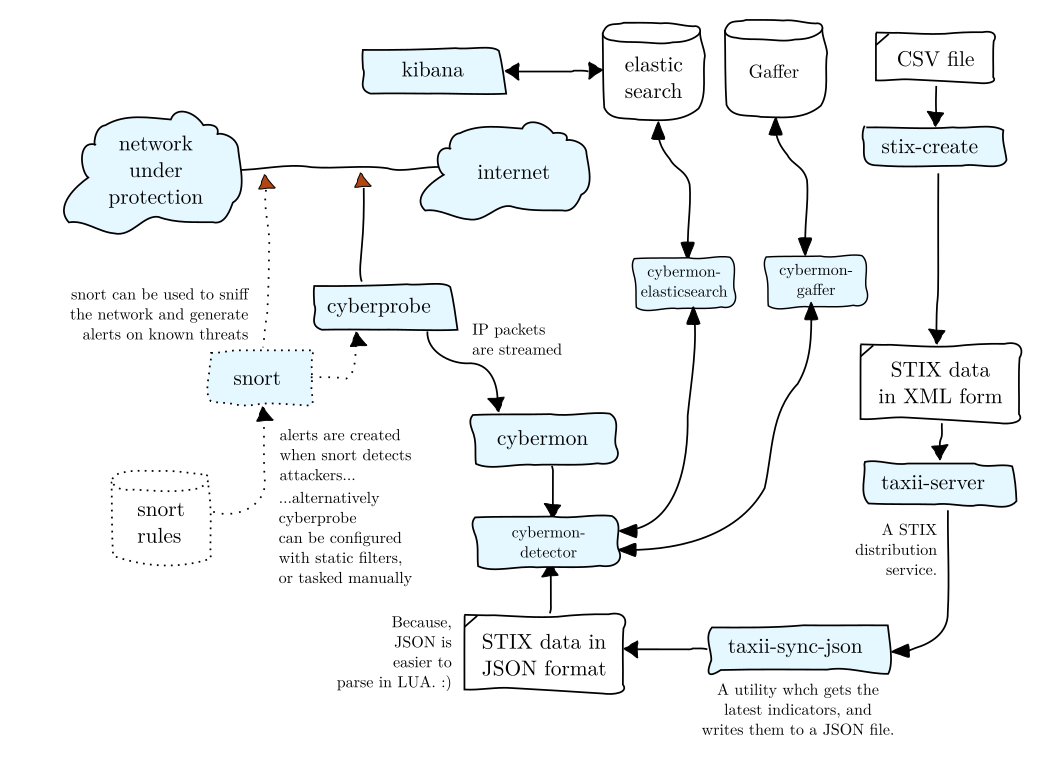
Cyberprobe consists of a set of loosely-coupled components which can be used together. We prefer to use simple interfaces, and prefer to use interfaces which are standards. Here's how we envisage these components being used:
cyberprobe - is a network sniffer which collects packets
which match an IP address list. The packets collected are streamed using
network streaming protocols. The IP address match list can be statically
configured (in a configuration file), can be dynamically changed using a
management interface, or can be dynamically changed as a result of Snort
alerts.
cybermon - receives packets from cyberprobe,
analyses them and generates session/transport level events which result in
user-configurable actions. For each event, a call is made to a Lua script
which the caller provides.
stix-db.lua - is a cybermon configuration file
we provide. It translates the cybermon events into a JSON
description which is fed into an ElasticSearch database. This configuration
file also reads a STIX configuration file for cyber threat indicators. When
these indicators are observed, the indicator meta-data is also added to the
JSON events.
taxii-server - is a TAXII compliant server, which is used
to distribute STIX rules over HTTP.
taxii-client-json - is a TAXII compliant client, which
fetches STIX data over TAXII and write it to a JSON file in a way that
stix-db.lua can read.
snort - is not part of cyberprobe, but it's a great NIDS, so
we use that.